Targeted attacks (watering hole) against S.Korea national security institutes are emerged in 16 May.
We worried about wrong information at this article: http://threatpost.com/ie-8-zero-day-pops-up-in-targeted-attacks-against-korean-military-sites/
A word 'Watering hole' means the infection attempts on the sites where the visitors are specific. In other words, the attacks lead to infect not normal peoples, but peoples are in specific stratum. In Korea, attacks against the game users are already detected since 2005. And the attack called 'Drive-by Download' that allows people infected just by visiting is widely issued globally. More broad and anonymous attacks are detected in Korea every week.
16 May 2013, the day before the national holiday, the attacks targeted against national security institutes are emerged and more several issues are detected. This attack can be defined as a watering hole because normal users are rarely visiting the national security institute's web sites.
Until these days, at least four national security institutes are detected as victims and more victims may exist. But four victims are founded based on the PCDS(Pre Crime Detect Satellite) until now and attacks are covertly and persistently made up.
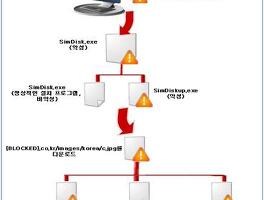
There are two types of malicious links injected by the alteration of the compromised web site's source codes. The one uses the shorten URL that redirect to the same malicious link. Usage of shorten URL for the malicious purpose is pointed out because of the security problems, but it is pregnant that shorten URL for the malicious link is used in PC environment, not mobile area for the malicious application installation, because it is used for avoid the detection.
The victims are KIMA(Korea Institute for Military Affairs), KINSA(Korea Institute for National Security Affairs), KRIS(Korea Research Institute for Strategy) and KIMS(Korea Institute for Maritime Strategy). These are specific purpose institutes that normal peoples are rarely visited.
The attackers have the privileges to change the web site's source codes and inject malicious link for drive-by downloads. There attacks have purpose of malware infection for targeted victims, not just change the web site's front page.
There are two Oracle Java vulnerabilities CVE-2013-1493 and CVE-2013-2423 are used to attack. Details of vulnerabilities are founded in http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2013-1493 and http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2013-2423.)
The malicious link used is already detected from PCDS in April, but the link is registered as an abnormal link because there are no exploit codes at that time. But the exploit codes are added and it may have more unrevealed attacks prior to 16 May.
The first detected malicious link in April is 'www.sunshop.com.tw/images/header.js'. This link is founded some of the four national security institutes issued now. The attackers remain that the malicious link have no exploit codes and they inject exploit codes to header.js file in 16 May to attack. More attacks are expected prior to April because PCDS already detected. The binary that executed after exploit is estimated as a backdoor.
Some parts of exploit codes used for Oracle Java vulnerability is as follows.
<html><head></head><body><applet archive="OS7aOmC5UPE2iQDJ.jar" code="Init.class" width="1" height="1"></applet><applet archive="0DUIOMCiPZUXfBvE.jar" code="Xxploit.class" width="1" height="1"></applet></body></html>
At least four national security institutes and the malicious link which related to Taiwan is blocked and additional actions are made up.
Form this case, the targeted attack not only e-mail attached attacks targeted major agencies, but also targeted specific visitors like watering hole is on the rise seriously. The problem is more complicated because there are rarely had the protection systems compared to e-mail attacks.
Also this type of attack is advanced that they add exploit codes when decided to attack and they use shorten URL to avoid detection.
The persistent attacks targeted major agency and corporations are covertly on going. Moreover follow attacks after 20 March incident raise the concerns about reaction plans.
The scalable infection mechanisms are started from the injection of malicious link to the compromised web site. If we can't block the entrance path of compromised web sites, the same incidents are going on and on. Also the information which leaks contains professional ones because the attack is targeted.
The attacks through the injection of malicious link to compromised web sites are widely used and it is difficult to detect that the shorten URL is malicious or not. Most people have no idea that they can be infected just by visiting compromised web sites.
The malicious link that redirected from the normal web site uses several application vulnerabilities of victim environment to download and execute automatically. And it is hard to react because the malware executed is made to avoid major anti-virus protections.
The attacks are valid to every people who visit the compromised web sites and they can be infected if they have just one of vulnerabilities. The additional losses are expected because attacks have all privileges after infection.
From the aspects of reaction, they have to solve this problem through the cooperation of the professional agency or corporation if they can't find the solution themselves. If the fundamental causes are not fixed, continuous malicious distribution and information leakage have to be considered.
'Security Indicator > Insight' 카테고리의 다른 글
| 6.25 사건 이전의 징후에 대한 팩트 정보 ( Red October 류의 백도어 포함) (0) | 2013.07.03 |
|---|---|
| 6.25 사이버 공격에 대한 다른 시각과 분석 (0) | 2013.07.02 |
| IE 8 노린 제로데이 공격, 국내서 발생 (5월 3주차) (0) | 2013.05.22 |
| 안보 관련 연구소 대상 표적공격 (워터링 홀) 5월16일 발생- 기사원문 (0) | 2013.05.22 |
| 3.20 대란 초기 경고 및 추적, 대응 히스토리 (요약) - 빛스캔 (0) | 2013.04.02 |